YubiKey 5 FIPS Series
Provide your organization with the highest level of authentication using keys with the FIPS 140-2 standard
About YubiKey 5 FIPS Series
The YubiKey 5 FIPS Series is a hardware-based authentication solution that provides the highest protection against account takeover and enables compliance with regulatory requirements. YubiKey offers strong authentication with support for multiple protocols, including existing Smart Card/PIV and FIDO2/WebAuth, the latest standard allowing for the replacement of weak password-based login with passwordless login. YubiKey is easy to use, fast, and reliable, proven on a large scale, significantly reducing IT costs and eliminating account takeovers.
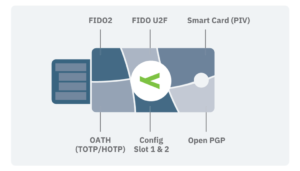
- Supports multiple older protocols such as OTP or TOTP/HOTP, OpenPGP, as well as modern ones: Smart Card/PIV, FIDO2/WebAuth, and FIDO/U2F,
- United States Government Certification: FIPS 140-2,
- Connectors: USB-A, USB-C, NFC, Lightning,
- IP68 protection grade, crush resistance, no batteries required, no moving parts.


FIPS 140-2 Standard
The Federal Information Processing Standard 140-2 (FIPS PUB 140-2) is an American computer security standard used to approve cryptographic modules. The FIPS 140-2 security requirements cover 11 areas related to the design and implementation of a cryptographic module.
Yubico products
Ask for a quote
Let's talk about a solution for your organization.
Protect against unauthorized access and ensure your organization's security.
How does YubiKey work?
Forget about having to reach for your phone, remembering and entering codes – just one touch of the YubiKey is enough to verify the user and it’s done. Moreover, you don’t have to use YubiKey every time. Once verified, an app or service can remain trusted.
YubiKey is available in various formats, supporting multiple authentication protocols and compatible with hundreds of applications and services. The models are dust and water-resistant, require no charging, cannot be disassembled, nor do they require driver installation – they are simple to use and configure.
Changing the game for modern authentication resistant to phishing
YubiKey is a revolutionary hardware solution that redefines the concept of authentication. It provides extremely effective protection of employee and user identities while reducing technical support costs and delivering unparalleled user experience.
For your Organization
92% reduction in calls to technical support
4 times faster login
High level of protection against phishing
No account takeovers

Highest authentication
Approved in accordance with FIPS 140-2 (Overall Level 1 and Level 2, Physical Security Level 3) Meets the highest level of Authenticator Assurance Level 3 (AAL3) according to NIST SP800-63B guidelines.
Strong two-factor authentication
A hardware token offering one-touch authentication. It does not require a battery or network connection.

Reduces IT costs
Reduces password support incidents by 92% and significantly lowers IT support costs

Yubico offers the following authentication options
- Strong single-factor authentication – passwordless
YubiKey replaces weak passwords with secure, passwordless login via touch.
- Strong two-factor authentication – password + token
YubiKey adds a second factor to two-factor authentication.
- Strong multi-factor authentication – passwordless + PIN
Combines touch-based authentication with PIN code authentication to meet the requirements for the most risky operations.
YubiKey supports the following authentication protocols:
FIDO U2F/FIDO2 U2F,
Yubico OTP (one-time password), HOTP (time-based or event-based token),
PIV (smart card) – the ability to store a PIV certificate on the key, which allows you to log in, among other things, to Active Directory,
Static passwords – keys from the 5 series have the ability to store a maximum of two long character strings, which can later be ‘injected’ into the user interface,
Challenge-Response – a login method that requires authorization from both sides (the key and the application), based on a ‘password-response’ principle,
OpenPGP – the ability to store a PGP key, used for encrypting emails, files, as well as signing them.
Get in touch with us
Would you like to learn how to improve security levels in your company?
We encourage you to get in touch with us – we are ready to answer any questions and provide professional advice in choosing the right solutions for your organization!




